In the early 2020s, quantum computing became a substantial issue surrounding the stability of Bitcoin, which counts on the SHA-256 cryptographic hash function for its proof-of-work agreement system. The security of Bitcoin is essentially connected to computational power, raising concerns about the prospective vulnerabilities postured by improvements in quantum innovation.
As an innovation that might bypass traditional double stars, quantum computing provides a possibility of interfering with recognized cryptographic approaches. However, the level of this risk goes through discuss.
One may ask whether quantum computing has the prospective to render Bitcoin a useless entity. To address this problem, it is essential to comprehend the dependence of Bitcoin on cryptography.
Bitcoin’s Bits and Hashing
When an image is referred to as being 1 MB in size, it is basically made up of around 1,000,000 Bytes. Given that each Byte makes up 8 bits, a picture of this size incorporates around 8,388,608 bits. Bits, the binary digits representing either 0 or 1, make up the essential systems of info in the digital world.
For an image, these bits appoint particular colors to specific pixels, rendering the image interpretable to the human eye. Conversely, a cryptographic function like SHA-256, established by the NSA, produces a steady output of 256 bits (or 32 Bytes) from an input of approximate size.
The main function of a hash is to transform differing strings of letters or numbers into a fixed-length output. Such obfuscation is perfect for compact information storage and anonymized signatures, and due to the nature of hashing, the procedure is unidirectional, rendering the resultant information successfully irreparable.
When describing SHA-256 as providing 256-bit security, it signifies that there are 2256 prospective hashes to be assessed for turnaround. Each Bitcoin deal produces a unique block hash by means of SHA-256, where the Merkle root, timestamp, nonce worth, and other metadata add to this unique hash.
An enemy trying to jeopardize the blockchain would require to recalculate hashes and extract needed information not just for the affected block however also for all subsequent blocks in the chain. Consequently, the enormity of the computational possibilities (2256) provides an extremely not practical difficulty, requiring incredible energy and time financial investments.
However, the development of quantum computing raises concerns concerning the practicality of this protective structure.
New Quantum Paradigm for Computing
Quantum computing diverges from the binary paradigm, presenting qubits, which make use of the concepts of superposition. Unlike standard bits that represent certain states of 0 or 1, qubits can exist in a superimposed state, permitting an indeterministic computing method.
Because qubits can be knotted and superimposed, calculations carried out on them end up being probabilistic. This particular permits a quantum computer system to process numerous states in parallel, possibly examining 2n mentions at the same time, where n shows the overall variety of qubits.
A standard binary computer system would require to participate in consecutive processing for each possible state, whereas a quantum computer system can simultaneously examine them. This transformative capacity was acknowledged in 1994 when mathematician Peter Shor presented an algorithm developed to enhance this procedure.
Shor’s algorithm utilizes methods such as Quantum Fourier Transform (QFT) and Quantum Phase Estimation (QPE) to speed up pattern acknowledgment, in theory jeopardizing cryptographic systems, consisting of however not restricted to Bitcoin.
Nevertheless, a substantial obstacle continues: the dependence on the stability and dependability of quantum computing.
Stabilizing Coherence in Quantum Computing
The idea of qubit superposition can be analogized to the action of turning a coin. While air-borne, the coin embodies both states—heads and tails—up until it settles and exposes a conclusive result.
Similarly, when qubits are solved, their superposition collapses into a classical state. However, for groundbreaking algorithms such as Shor’s to work successfully, preserving various qubits in their superposition states over a prolonged period for interactivity is important; otherwise, important computations might stop working to finish.
This circumstance highlights problems surrounding quantum decoherence (QD) and quantum mistake correction (QEC). Moreover, these technical difficulties should be prevailed over throughout lots of qubits to help with complicated calculations.
A research study entitled Millisecond Coherence in a Superconducting Qubit, released in June 2023, reported an optimum coherence time of 1.48 ms at a typical gate fidelity of 99.991%, showing the dependability of a quantum processing system (QPU).
Currently, IBM’s Quantum System Two sticks out as the most sophisticated quantum computing architecture. This modular system is poised for scaling, intending to perform 5,000 operations utilizing 3 Heron QPUs in a single circuit by the end of 2024, with an enthusiastic objective of reaching 100 million operations by 2033.
The important concern stays: will this ability sufficiency enable the useful execution of Shor’s algorithm to jeopardize Bitcoin?
QC Threat Viability
At present, due to the difficulties postured by decoherence and fault tolerance, quantum computer systems do not make up a significant risk to existing cryptographic systems. The expediency of producing a fault-tolerant quantum system at scale stays unsure, especially offered the rigid ecological pureness needed.
This pureness is impacted by elements such as electron-phonon scattering, photon emissions, and inter-electron interactions. Notably, as the variety of qubits boosts, which is essential for Shor’s algorithm, so too does the problem of decoherence.
Despite these substantial obstacles, significant improvements in QEC methods are being made. For circumstances, Riverlane’s Deltaflow 2 technique permits real-time QEC on approximately 250 qubits. By 2026, it is expected that this development will yield the very first feasible quantum application with countless real-time quantum operations (MegaQuOp).
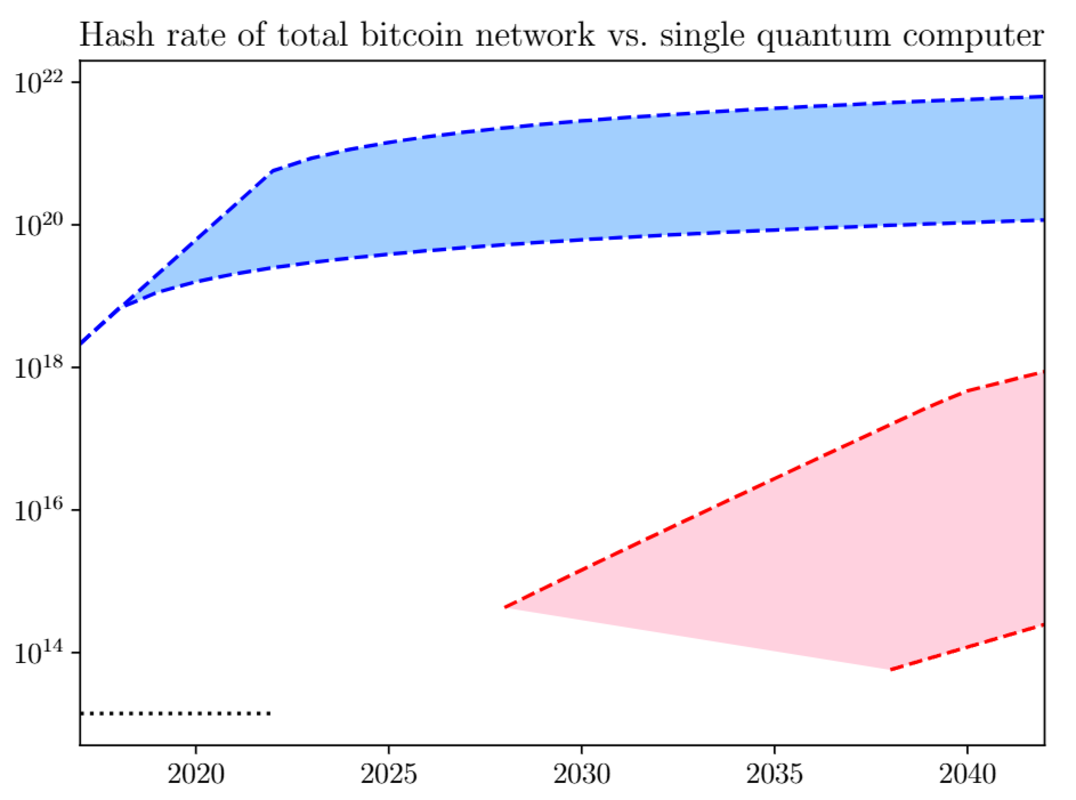
According to a post by AVS Quantum Science released in January 2022, around 13 million qubits would be needed to perform an effective attack versus SHA-256 within a single day. More dauntingly, near 1 billion qubits would be essential for a 51% compromise of the Bitcoin mainnet.
Regarding the execution of the Grover algorithm, which takes advantage of quantum computing to check out disorganized databases (such as special hashes), a research study publication in 2018 recommended that no quantum computer system would can performing it successfully up until a minimum of 2028.
Image credit: Ledger Journal
While the Bitcoin network’s hashrate has actually considerably increased because that time, and quantum computing faces decoherence as a main challenge, the prospective development of dependable quantum systems requires active readiness versus prospective dangers to Bitcoin.
Quantum Computing Resistance
Various methods have actually been proposed to secure Bitcoin holders versus the advances of quantum computing. Given the low possibility of a 51% quantum attack, existing efforts mainly concentrate on improving wallet security. The total sustainability of Bitcoin relies greatly on users’ self-confidence in the security of their holdings; a loss of this self-confidence might cause an extreme decrease in BTC’s worth and a matching decrease in network hashrate, increasing vulnerability to quantum attacks.
One technique proposed to reinforce security is using Lamport signatures. This method produces a personal crucial paired with 512 bitstrings originated from a single 256-bit output. A public secret is created for each of the 512 bitstrings through a cryptographic function, needing a unique Lamport signature for each Bitcoin deal.
Since Lamport signatures do not count on elliptic curves, which are utilized in the Elliptic Curve Digital Signature Algorithm (ECDSA) presently utilized by Bitcoin and possibly susceptible to Shor’s algorithm, however rather on hash functions, they provide a practical alternative resistant to quantum dangers.
Nonetheless, Lamport signatures include particular downsides, consisting of increased size—possibly going beyond 16KB—and the restriction of single-use performance. Additionally, merely moving addresses and using freezer can alleviate prospective quantum dangers by securing personal crucial direct exposure.
Another possible reaction to threatening quantum attacks is the adoption of lattice-based cryptography (LBC). Unlike ECDSA, LBC does not count on limited patterns however uses discrete points in a boundless n-dimensional lattice, making it resistant to recognized quantum algorithms efficient in jeopardizing existing cryptographic structures.
However, any shift to brand-new cryptographic requirements would need a substantial adjustment to Bitcoin’s codebase, requiring a tough fork. Such a shift would likely require significant signals showing impending improvements in quantum computational abilities, especially concerning qubit amount and fault tolerance.
Bottom Line
Currently, it can be concluded that the Bitcoin mainnet is not under impending risk from quantum computing, neither in the near nor long run. However, should quantum computing effectively weaken Bitcoin’s file encryption—reducing the effectiveness of SHA-256 and ECDSA—this might badly affect user self-confidence in the cryptocurrency.
Confidence in Bitcoin is critical, as evidenced by the involvement of significant corporations like Microsoft and PayPal, which have actually embraced Bitcoin payments due to significant expense savings and improved monetary control. With over 300 million holders worldwide, Bitcoin keeps its position as both a safe and secure property and an affordable payment option.
Ultimately, the worth of Bitcoin is sustained by the capital expense and the self-confidence of its user base. The historic volatility of Bitcoin shows that numerous occasions—varying from prominent tweets to substantial business combinations—have significant results on market belief. A severe risk to Bitcoin’s file encryption might speed up a wave of sell-offs, miner withdrawals, and lowered mining problem, possibly assisting in a 51% quantum attack with a decreased qubit requirement.
In light of these factors to consider, it is recommended for Bitcoin holders and designers to stay alert concerning improvements in quantum computing.
This is a visitor post by Shane Neagle. The views revealed herein show the author’s viewpoint and do not always represent those of BTC Inc. or Bitcoin Magazine.
Thank you for visiting our site. You can get the latest Information and Editorials on our site regarding bitcoins.