For anybody with considerable bitcoin holdings, a custody structure that consists of a single point of failure must be viewed as inappropriate. If a wallet has a single part that—when lost or taken—can result in an irreversible loss of funds, then it’s just too unsafe to think about. Nobody wishes to keep substantial wealth teetering on the edge of disaster.
Individual bitcoin holders have many tools offered that can help in reducing the threat of loss or theft. In a previous post, we covered a few of these tools, highlighting adjustments typically used to singlesig wallets. However, we also discussed why these methods disappoint eliminating single points of failure completely.
For a company, federal government, or other organization that wishes to protect a bitcoin treasury, removing single points of failure is not simply a nice-to-have, however a requirement. The just custody designs worth thinking about for these entities are ones that consist of a limit requirement in order to gain access to funds. A limit requirement explains a structure that includes numerous, independently protected parts, where a subset of those parts are required to authorize any withdrawal. This is the only method of attaining institutional-grade security, with single points of failure got rid of entirely.
In this post, we’ll cover how to use threshold security utilizing 3 various techniques: script multisig, Shamir’s secret sharing (SSS), and multi-party calculation (MPC). We’ll also dive into the tradeoffs related to each method, and how an organization can pick the very best setup to satisfy their requirements.
What is multisig?
If you aren’t sure what script multisig is, we suggest taking a look at our earlier post committed to describing how multisig wallets work and what they’re utilized for. As a fast evaluation, a multisignature wallet includes numerous personal secrets, and can be set up so that a particular number (limit) of those personal secrets are needed to sign any deal. The signatures can be produced at various times and areas, permitting each secret to stay physically separated. Once a limit variety of signatures have actually been produced, they can be integrated into a single bitcoin deal efficient in investing the funds.
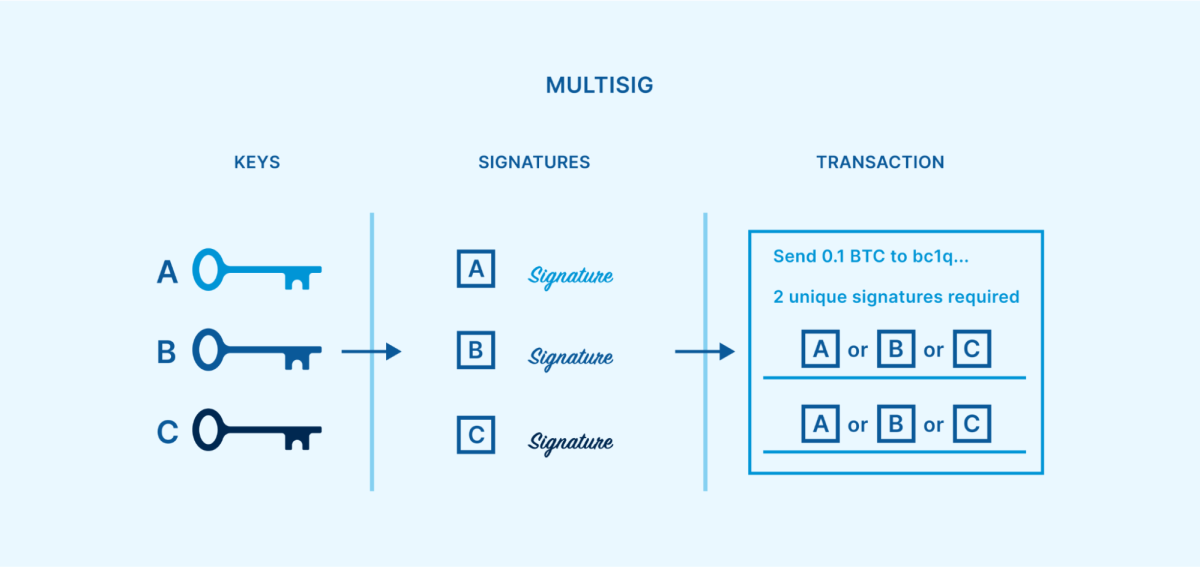
This reasonably basic method of developing a limit requirement is extremely efficient at eliminating all single points of failure. As long as the costs limit is higher than one however less than the overall variety of secrets, then any single secret can end up being lost, taken or damaged without bitcoin ending up being unrecoverable. The staying secrets might sign a healing deal moving funds to a fresh multisig setup.
Satoshi Nakamoto prepared for multisig when bitcoin was very first launched, expecting that it might be a popular system for protecting funds. However, it wasn’t till the P2SH softfork in 2012 that multisig began to end up being a commonly utilized tool. Multisig has actually given that shown itself as a battle-tested security design for more than a years, throughout numerous various address types.
What is Shamir’s secret sharing?
Shamir’s secret sharing (SSS) is a secret sharing algorithm that was established by popular cryptographer Adi Shamir in 1979. It can be utilized as another method of presenting a limit requirement for safeguarding bitcoin. SSS permits users to divide a secret into numerous dispersed “shares,” with just a specific limit of the shares required to reassemble the secret. This can be utilized to create quorums like 2-of-3 or 3-of-5, comparable to multisig.
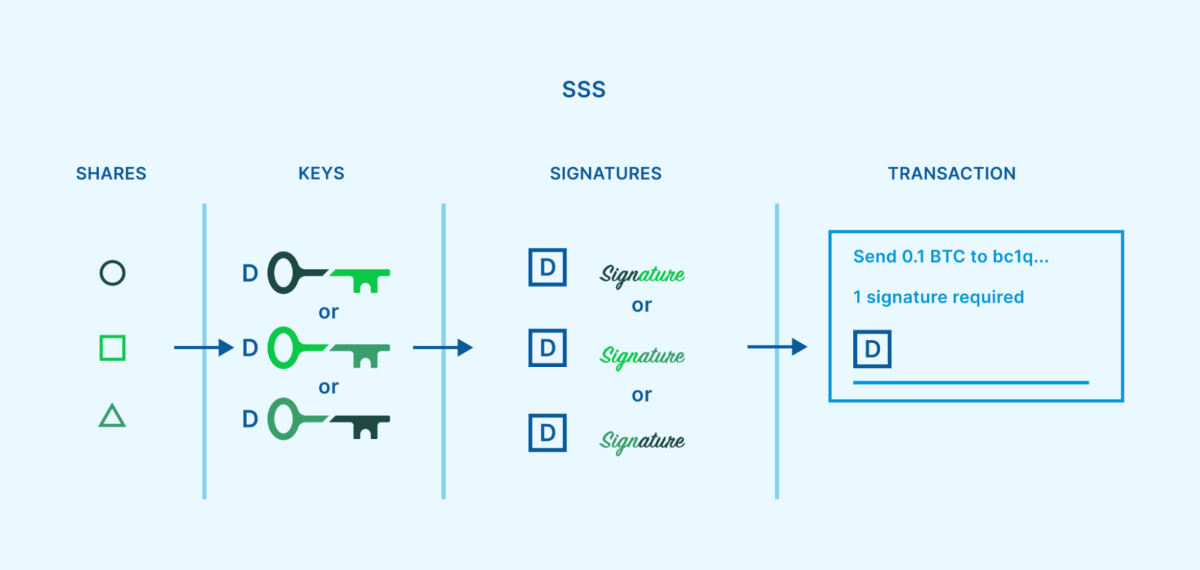
However, this method still results in single points of failure at specific circumstances throughout its lifecycle. One example is when the secret is at first broken up into SSS shares. This operation is generally done on a single gadget at a single time and location. If an assaulter compromises that gadget, the crucial generation procedure or the share production procedure, they’ve jeopardized the secret. Another example is whenever the user requires to reassemble the secret to sign a deal. A limit variety of shares should be united, as soon as again on a single gadget at a single time and location, which an assaulter might make use of.
A relatively basic and commonly utilized approach of executing SSS innovation for cryptocurrency custody is through the Shamir backup, established by Satoshi Labs in 2017. It can be discovered as a choice in specific Trezor hardware wallet designs.

What is MPC?
MPC, or multi-party calculation, is a subfield of cryptography that traces back to the 1970s. The objective of MPC is to permit numerous individuals to collectively carry out a calculation, while each individual’s contribution to the calculation is not exposed to the remainder of the group and for that reason can stay personal. This permits numerous celebrations to team up in numerous contexts without requiring to rely on each other.
When used to bitcoin custody, MPC includes dispersed “shares,” comparable to SSS. However, unlike SSS, the shares are not divided from a personal crucial nor secondhand to reconstruct a personal secret. Instead, numerous celebrations calculate a single signature straight from a limit of their shares.
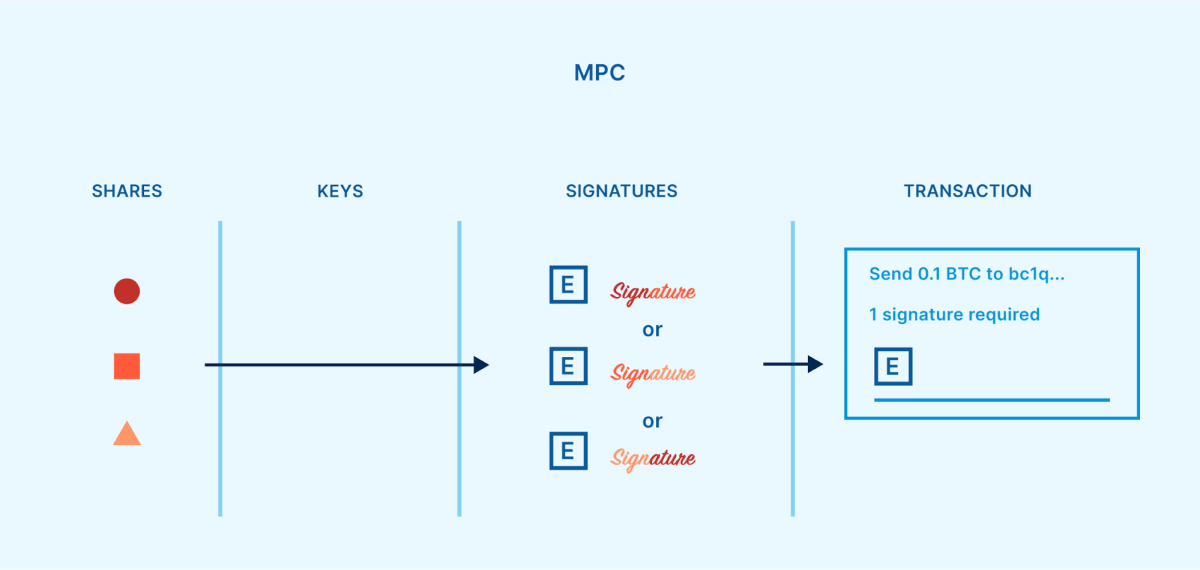
Unlike SSS, MPC does not demand a single point of failure. MPC shares can be created independently from one another, and they never ever require to be united to run the wallet. Information produced from a share can be interacted to the other individuals, without the share itself being exposed.
Since bitcoin and other cryptocurrencies have actually mostly utilized a signature system based upon ECDSA (Elliptic Curve Digital Signature Algorithm), MPC needed to be adjusted for this context. The very first useful limit procedures for ECDSA were released in 2018. [GG18, LNR18]
What are the compromises in between limit designs?
With 3 various limit security designs to select from, the next action is comprehending the strengths and weak points of each alternative.
Tradeoffs with multisig
Script multisig is a standardized method of attaining threshold security, belonging to the bitcoin procedure. The structure is thought about reasonably basic and robust. The barrier to entry is also little—if a bitcoin user understands how to run a singlesig wallet, then it’s not a big leap to find out how to establish and utilize a multisig wallet.
When a multisig wallet is initialized, the addresses produced for getting bitcoin into the wallet have the limit requirement developed into them. Once a multisig address has actually been moneyed, the bitcoin is safeguarded by an immutable agreement that has actually basically been composed into the blockchain itself. The just method to change the agreement (such as altering the gain access to control policy, changing which secrets are safeguarding the bitcoin) is to move the bitcoin to a brand-new address that was developed with a various agreement. For numerous celebrations who are working together to protect bitcoin, this ground-level immutable agreement system can offer the greatest degree of peace of mind that the cash is protected according to how all celebrations have actually meant. If anything were to be basically altered, it would end up being apparent to everybody by the event of a public deal, and the secrets that authorized the modification would be understood. This is why collective custody suppliers such as Unchained count on script multisig for our items.
However, releasing agreements openly on the blockchain includes tradeoffs. As bitcoin is invested out of a multisig address, the gain access to control policy for that address should be completely released on the blockchain. Observers can then see the information of the multisig quorum that was being utilized. Although the staying funds can be quickly moved to a brand-new address moving forward, the reality that previous security plans are exposed isn’t perfect. Additionally, requiring to move bitcoin from one address to another in order to change the gain access to control policy implies that deal charges are constantly included with the procedure (and the bigger the quorum, the more pricey it will be).
For entities that worth custodying altcoins, such as cryptocurrency exchanges, script multisig can posture more of an obstacle than the other 2 techniques of limit security. This is due to the fact that a multisig limit quorum is troubled the blockchain level, and various cryptocurrencies utilize various blockchains. Many cryptocurrencies don’t even support a native, robust multisig execution at all. Meanwhile, SSS and MPC implement limit quorums at the crucial level, and appear like singlesig deals openly. Since nearly all cryptocurrencies support a comparable requirement for singlesig custody (the exact same secret can be utilized throughout the majority of cryptocurrencies), this permits SSS and MPC to be more cross-chain suitable.
Tradeoffs with Shamir’s secret sharing
SSS uses another method of creating a limit requirement based upon reasonably basic and battle-tested cryptography. For the functions of cryptocurrency custody, SSS also has actually a commonly released approach with a low barrier to entry (Shamir backup). Once somebody has experience utilizing a standard singlesig wallet, it isn’t a big leap to utilize a Trezor to establish a wallet with a Shamir backup.
Unlike multisig, SSS runs entirely beyond public-facing addresses and deals on the blockchain. Instead, the limit requirement is chosen by how the personal secret is divided into shares. This implies that splitting a secret into shares and later on reassembling them can be performed in personal, so that just individuals taking part in the bitcoin custody plan know that SSS is being utilized. In addition to personal privacy benefits, keeping the limit structure beyond the blockchain also implies that SSS deals won’t result in increased charges, and it can be utilized to protect various cryptocurrencies. Although most cryptocurrencies have their own special blockchains, they can all share the exact same personal secret as a gain access to point, which secret can in turn be broken up utilizing SSS.
The most significant drawback to SSS has actually currently been pointed out above—the personal secret should exist in one location at one time, before it is very first split into shares, and also when the shares are recombined for the functions of authorizing a withdrawal. These vulnerabilities develop short-lived single points of failure, suggesting that SSS by itself doesn’t provide genuinely institutional-grade security, unlike multisig or MPC.
Additionally, SSS doesn’t natively provide a technique for changing the gain access to control policy. Once a personal secret is divided into a quorum of shares, those shares will constantly preserve the capability to replicate that secret. If a group is protecting a treasury together utilizing SSS and a member of the group leaves, withdrawing consents for that person in a safe way can posture an obstacle. Remaining members of the group might reassemble the secret and after that divided it into brand-new shares, however the old shares would require to be verifiably damaged. Otherwise, the funds would require to be sent out to a completely brand-new wallet safeguarded by a various secret.
Tradeoffs with MPC
Much like SSS, MPC imposes the limit requirement at the key-level rather of the blockchain-level. This opens comparable benefits, such as approving a greater capability for personal privacy, preventing increased deal charges, and permitting one MPC custody structure to be utilized throughout various cryptocurrencies.
Importantly, MPC handles to prevent the short-lived single points of failure that include utilizing SSS. By utilizing a various cryptographic approach, the crucial shares can exist independently from the minute the wallet is very first developed, and even stay different while signing withdrawal deals. Most MPC applications also consist of a native approach of changing the gain access to control policy (developing a brand-new quorum of shares) without needing to send out funds to a brand-new wallet address.
However, MPC for limit ECDSA is thought about extremely intricate cryptography, and there is not an agreed-upon requirement for utilizing it. There are various procedures, with the very first 2 being established individually in 2018 by Gennaro and Goldfeder [GG18] and Lindell et al. [LNR18]. Since then, we’ve also seen procedures from Doerner et al. [DKLs19], Castagnos et al. [CCL+20], Damgård et al. [DJM+20], Canetti et al. [CMP20], Gągol et al. [GKSS20], Gennaro and Goldfeder [GG20], Canetti et al. [CGG+21], Abram et al. [ANO+21], Doerner et al. [DKLs23], and maybe others. While the more recent procedures tend to ensure enhancements upon the older ones, they might have had less chance for peer-review, audit, and other screening.
The greater level of intricacy included with MPC develops a broadened attack surface area. With extra parts and treatments, there is more space for mistake and prospective security vulnerabilities. Evidence of major security defects, consisting of complete personal crucial extraction attacks, has actually currently emerged more than as soon as, impacting a few of the limit ECDSA procedures noted above.
Examples consist of:
AS20 vulnerabilities, September 2020, impacting GG18 applications
Alpha-Rays vulnerabilities, December 2021, impacting GG18 and GG20
TSSHOCK vulnerabilities, August 2023, impacting GG18, GG20, and CGG+21
BitForge vulnerabilities, August 2023, impacting GG18 and GG20
“Cryptography needs to pass the test of time to attain longevity, and these new protocols clearly didn’t pass the test of time[…] this research was not ready for implementation or widespread adoption. From my perspective, implementing and productizing such recent research is quite dangerous.” — Ledger CTO Charles Guillemet, December 2021 action to Alpha-Rays
“[MPC is] more complicated, more to get wrong. Advanced crypto protocols are fragile in the detail and in the implementation. I’d feel more confident in multisig, which is super simple and rock solid.” — Post by popular cryptographer Adam Back, January 2023
MPC is also restricted by who can reasonably utilize it in the very first location. As formerly pointed out, limit ECDSA is extremely made complex. For the typical specific, there are no tools offered to securely or quickly established MPC individually. While some organizations provide collective custody MPC wallets that are relatively simple to utilize, those organizations provide no simple method for users to recuperate funds if business vanishes (or no other way at all, in which case they are a single point of failure). Because script multisig is a basic and open requirement, organizations who offer collective custody services utilizing multisig can provide open-source and user friendly healing tools. This develops a simple opportunity for customers to recuperate their funds even if the collective multisig service were no longer offered to help.
Which design is finest?
As we simply covered, there are many tradeoffs in between utilizing multisig, SSS, and MPC. They can be set up in a chart for a visual contrast:
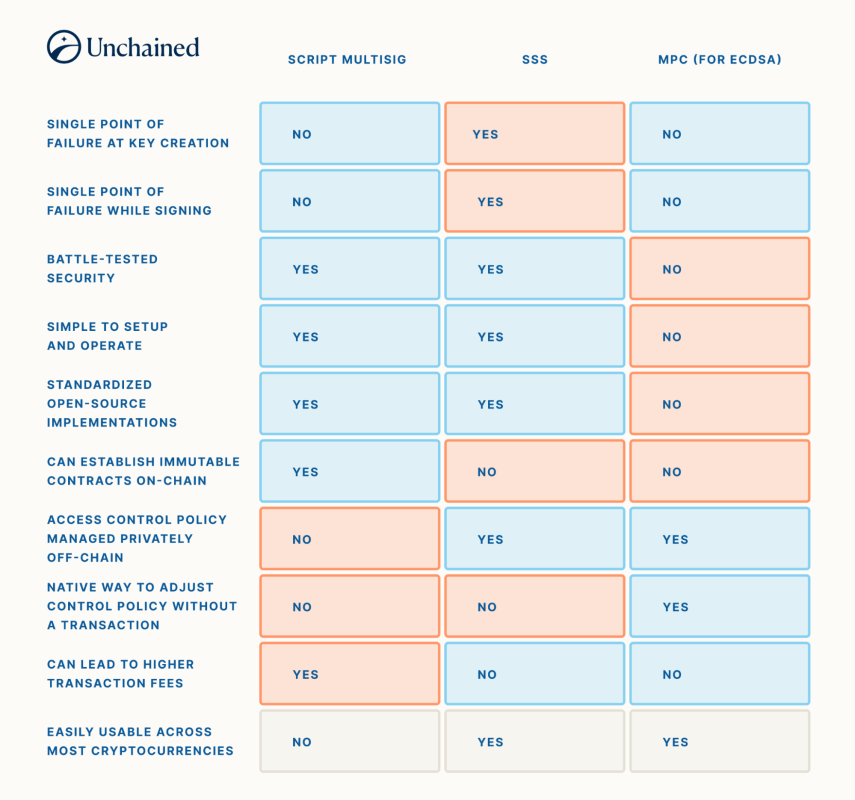
If a company concentrates on the custody of various cryptocurrencies, they may be encouraged to employ a group of specialists to thoroughly establish an MPC custody design. However, if a company or person were searching for a basic and trustworthy method to protect bitcoin for the long term, utilizing script multisig and accepting the personal privacy tradeoffs may be more suitable. SSS is hardly ever utilized by itself due to its failure to implement institutional-grade limit requirements at all times.
Combining designs for collective custody
While multisig, SSS, and MPC are frequently considered completing security designs, it’s possible to include more than among them into a general custody structure. As formerly explained, SSS and MPC permit a limit of crucial shares to produce a signature for a deal. If the signature was for costs funds out of a singlesig wallet, then absolutely nothing else would be needed to finish the deal. However, if rather the signature was for costs funds out of a multisig wallet, extra signatures from other secrets might also be required.
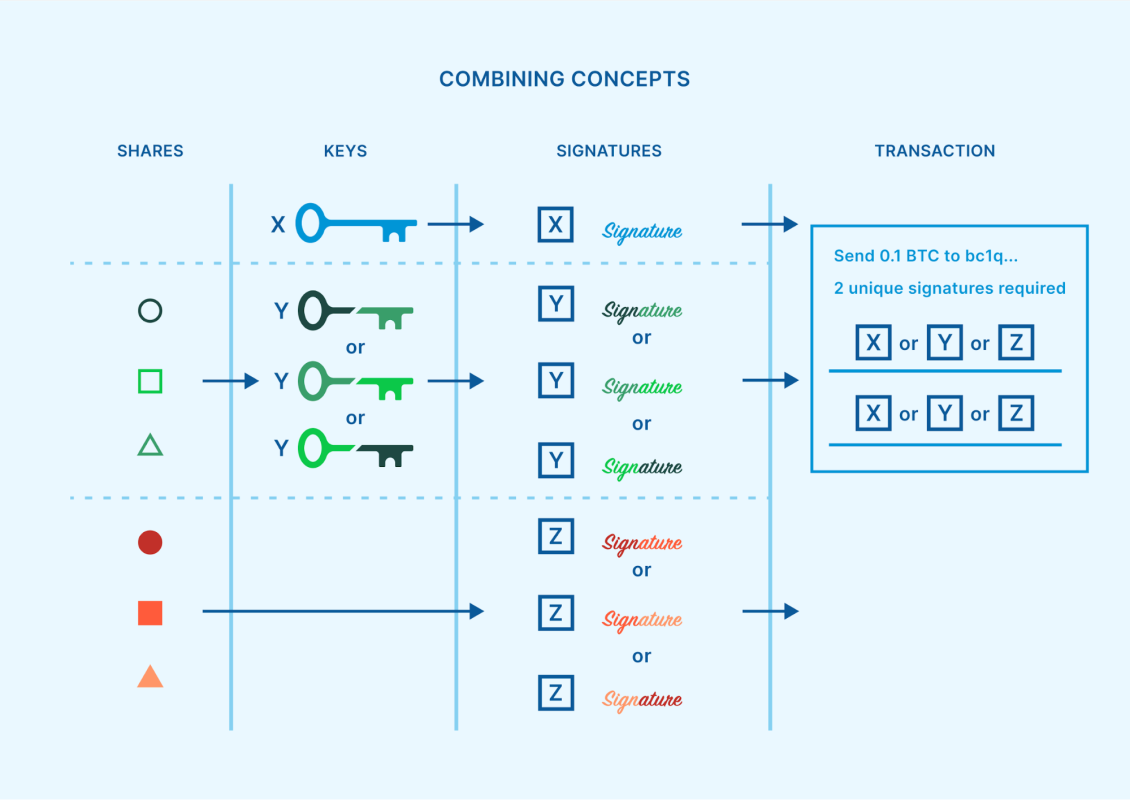
While this mix of methods might sound unneeded and troublesome, there are undoubtedly some contexts where it makes useful sense. With the increase in appeal of crucial representatives and multi-institution custody, there is a growing variety of specialized organizations that are commissioned by people and organizations to protect among the secrets to a multisig wallet. These dispersed crucial representatives can help in reducing custodial threat. But how should a crucial representative protect that single secret which they are accountable for?
SSS or MPC can be a technique to decrease or eliminate single points of failure from this task. A business crucial representative can create a system where numerous various officers within business each hold crucial shares, and for that reason a signature can just be produced upon arrangement from a limit of those officers. Additionally, if an attack were to happen throughout an SSS reassembly, or an MPC execution winds up experiencing a brand-new crucial extraction vulnerability like the ones noted previously, then no client funds are right away at threat. The crucial representative would have time to respond and resolve the problem, while the bitcoin stays safeguarded by the wider multisig wallet.
Using script multisig to develop a limit requirement as a fundamental immutable agreement, and after that commissioning expert crucial representatives to each secure a multisig secret utilizing their own SSS or MPC limit, is by far the most safe approach for an organization to keep bitcoin protected for the long-lasting.
New abilities with Taproot
In November of 2021, the Taproot soft-fork took place, including brand-new tools into the bitcoin environment. Some of these tools affect the future of institutional-grade bitcoin custody, by permitting specific enhancements and optionalities.
- Schnorr signatures: The Schnorr signature algorithm is now offered in bitcoin as an option to ECDSA. Using MPC on top of Schnorr results in threshold security plans that are far less complex, and for that reason also offer greater self-confidence in their security, compared to the ECDSA procedures pointed out previously. FROST is the leading Schnorr limit signature procedure, while MuSig2 is also offered particularly for N-of-N quorums. Both of these signature plans are on the course to ending up being standardized tools throughout the bitcoin market, and they are anticipated to make MPC offered for routine people, with a user experience comparable to script multisig.
- Script type personal privacy: Pay-to-Taproot (P2TR) addresses are a brand-new address type that permit script multisig bitcoin addresses to appear similar to the addresses being utilized for singlesig wallets. This supplies a substantial personal privacy enhancement, due to the fact that it implies that the bitcoin address itself doesn’t offer any hints about its owner’s security design, such as whether they may be utilizing script multisig.
- Multiple costs courses: P2TR addresses also have the capability to include numerous costs courses developed into them. This can develop brand-new methods of structuring threshold security for institutional-grade custody, as explained in BIP 342 (reasoning, area 5). For example, a user might develop an N-of-N script multisig costs course for every single mix of secrets that can invest funds. Rather than construct a 2-of-3 quorum with secrets A, B, and C, a comparable result can be attained with 3 different 2-of-2 quorums as possible costs courses—one with secrets A and B, one with secrets A and C, and one with secrets B and C. This technique can increase personal privacy, due to the fact that just the costs course that winds up getting utilized will be exposed. A comparable idea can be used to MPC crucial share quorums, permitting MuSig2 to be used for limits.
These Taproot tools are reasonably brand-new, and their adoption is still in the early phases. Many bitcoin software applications and services don’t yet provide complete assistance for what Taproot needs to provide. It’s also worth keeping in mind that the majority of altcoins don’t have these tools natively offered.
Final ideas
A growing variety of organizations are ending up being thinking about protecting a bitcoin treasury, and they need efficient services. Avoiding single points of failure and decreasing counterparty threat are vital factors to consider. The finest method to satisfy these requirements is by leveraging a multisig structure, where secrets can be dispersed amongst numerous business crucial representatives, none of whom will have unilateral control over the bitcoin. Each crucial representative can utilize SSS or MPC to include additional limit security for their specific secret.
Unchained has actually originated a business custody network, developed for institutional customers who wish to establish a plan like this. It’s simple to utilize and personalized, so that each customer gets to pick whether they’d like to hold a managing variety of secrets themselves, or simply a single secret, or leave the duty of protecting secrets completely as much as the numerous, independent business crucial representatives. If you’re interested in finding out more, schedule a complimentary assessment with us today!
Special thanks to Dhruv Bansal for examining this post and supplying important feedback.
Originally released on Unchained.com.
Unchained Capital is the main United States Collaborative Custody partner of Bitcoin Magazine and an important sponsor of associated material released through Bitcoin Magazine. For more details on services provided, custody items, and the relationship in between Unchained and Bitcoin Magazine, please check out our site.
Thank you for visiting our site. You can get the latest Information and Editorials on our site regarding bitcoins.

